Download Malware Effects Remediation Tool 4 full version program free setup for Windows. Malware Effects Remediation Tool is an Open Source tool meant for helping clean the after-effects of a malware infection.
Malware Effects Remediation Tool Overview
The Malware Effects Remediation Tool is a crucial software solution designed to combat and mitigate the impact of malicious software on computer systems. Developed with a focus on cybersecurity, this tool is engineered to detect and remediate the adverse effects of malware, which encompasses a broad range of malicious software including viruses, trojans, ransomware, and other cyber threats. One of the key strengths of this tool lies in its ability to swiftly identify and neutralize the effects of malware attacks, ranging from data breaches to system disruptions. The tool employs advanced algorithms and heuristics to analyze system behavior, identifying anomalous patterns indicative of malware presence. An essential aspect of the Malware Effects Remediation Tool is its comprehensive approach towards remediation. Rather than solely focusing on removing the malware itself, the tool is designed to address the residual impact, such as system vulnerabilities, unauthorized access points, and potential data corruption. This multifaceted remediation strategy enhances the overall cybersecurity posture of the affected system, fortifying it against future attacks. The tool often integrates with existing antivirus and security solutions, complementing their capabilities and providing an additional layer of defense.
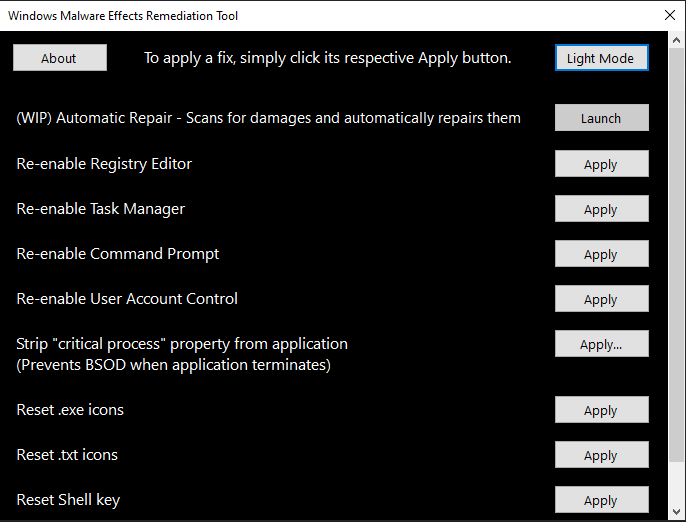
The user interface of the Malware Effects Remediation Tool is typically designed to be user-friendly and accessible, catering to both cybersecurity professionals and individuals with varying levels of technical expertise. It offers intuitive controls for initiating scans, reviewing reports, and implementing remediation measures. Real-time monitoring capabilities allow users to stay informed about ongoing threats and the tool’s proactive efforts to neutralize them. Furthermore, the tool may offer features such as quarantine functionality to isolate and contain infected files, preventing further spread within the system. Automatic updates ensure that the tool’s malware signature database stays current, enabling it to recognize and remediate the latest threats. Additionally, it may provide detailed reports and logs, offering insights into the nature of detected threats and the effectiveness of the remediation process.
In conclusion, the Malware Effects Remediation Tool stands as a frontline defense against the ever-evolving landscape of cyber threats. Its robust detection mechanisms, comprehensive remediation strategies, and user-friendly interface make it an indispensable component in the ongoing battle to safeguard computer systems from the detrimental effects of malware attacks. As cyber threats continue to advance in sophistication, the importance of such tools in maintaining the integrity and security of digital environments cannot be overstated.
Features
- Malware Detection: The tool employs advanced algorithms and heuristics for the effective detection of various types of malware, including viruses, trojans, and ransomware.
- Comprehensive Remediation: It goes beyond merely removing malware, addressing the residual impact such as system vulnerabilities, unauthorized access points, and potential data corruption.
- Anomalous Behavior Analysis: Utilizes behavior analysis to identify and neutralize malware by detecting abnormal patterns in system behavior.
- Cybersecurity Posture Enhancement: Enhances the overall cybersecurity posture of the system by fortifying against future attacks and improving resilience.
- Integration with Antivirus Solutions: The tool seamlessly integrates with existing antivirus and security solutions, providing an additional layer of defense and complementing their capabilities.
- User-Friendly Interface: Designed with a user-friendly interface, catering to both cybersecurity professionals and individuals with varying levels of technical expertise.
- Real-Time Monitoring: Provides real-time monitoring capabilities, keeping users informed about ongoing threats and the tool’s proactive efforts to neutralize them.
- Remediation Reports: Offers detailed reports on the remediation process, providing insights into the nature of detected threats and the effectiveness of the remediation measures.
- Quarantine Functionality: Includes quarantine features to isolate and contain infected files, preventing further spread within the system.
- Automatic Updates: Ensures that the tool’s malware signature database stays current, enabling it to recognize and remediate the latest threats.
- Proactive Threat Mitigation: Takes a proactive approach to mitigate threats before they can cause substantial damage to the system.
- Behavioral Analysis: Utilizes behavioral analysis to understand the actions and patterns of potential malware, aiding in more accurate detection.
- Heuristic Scanning: Incorporates heuristic scanning methods to identify new and previously unknown threats based on their characteristics.
- Zero-Day Threat Protection: Offers protection against zero-day threats by employing advanced detection techniques that do not rely on known signatures.
- Dynamic Threat Intelligence: Utilizes dynamic threat intelligence to stay updated on emerging threats and adapt its detection mechanisms accordingly.
- Memory Scanning: Scans system memory for signs of malicious activity, addressing threats that may attempt to reside in volatile memory areas.
- Registry and File System Analysis: Conducts in-depth analysis of the registry and file system to identify and remediate malware artifacts.
- Network Traffic Monitoring: Monitors network traffic for suspicious patterns and activities, identifying potential threats and attempting to communicate externally.
- Cloud-Based Threat Intelligence: Leverages cloud-based threat intelligence databases to enhance detection accuracy and response capabilities.
- Rootkit Detection and Removal: Specialized tools for detecting and removing rootkits, which often attempt to hide their presence on the system.
- Browser Extension Security: Offers protection against malicious browser extensions and plugins that may compromise online security.
- Secure Web Browsing: Enhances web browsing security by detecting and blocking access to known malicious websites.
- Email Attachment Scanning: Scans email attachments for malware, preventing malicious content from infiltrating the system through email channels.
- Sandboxing Technology: Uses sandboxing technology to isolate and analyze potentially malicious files in a controlled environment before allowing execution.
- Phishing Protection: Provides features to detect and block phishing attempts, safeguarding users against social engineering attacks.
- Endpoint Protection: Extends protection to various endpoints, including desktops, laptops, servers, and other devices connected to the network.
- Firewall Integration: Integrates with firewalls to enhance network security and control incoming and outgoing traffic.
- Multi-Platform Compatibility: Offers compatibility across multiple platforms, ensuring protection for a diverse range of operating systems.
- Incident Response: Includes incident response features, allowing for swift and effective responses to security incidents and breaches.
Technical Details
- Software Name: Malware Effects Remediation Tool for Windows
- Software File Name: Malware-Effects-Remediation-Tool-4.0.1.rar
- Software Version: 4.0.1
- File Size: 2.10 MB
- Developers: github
- File Password: 123
- Language: Multilingual
- Working Mode: Offline (You donÆt need an internet connection to use it after installing)
System Requirements
- Operating System: Win 7, 8, 10, 11
- Free Hard Disk Space:
- Installed Memory: 1 GB
- Processor: Intel Dual Core processor or later
- Minimum Screen Resolution: 800 x 600
What is the latest version of Malware Effects Remediation Tool?
The developers consistently update the project. You can view the most recent software update on their official website.
Is it worth it to install and use Software Malware Effects Remediation Tool?
Whether an app is worth using or not depends on several factors, such as its functionality, features, ease of use, reliability, and value for money.
To determine if an app is worth using, you should consider the following:
- Functionality and features: Does the app provide the features and functionality you need? Does it offer any additional features that you would find useful?
- Ease of use: Is the app user-friendly and easy to navigate? Can you easily find the features you need without getting lost in the interface?
- Reliability and performance: Does the app work reliably and consistently? Does it crash or freeze frequently? Does it run smoothly and efficiently?
- Reviews and ratings: Check out reviews and ratings from other users to see what their experiences have been like with the app.
Based on these factors, you can decide if an app is worth using or not. If the app meets your needs, is user-friendly, works reliably, and offers good value for money and time, then it may be worth using.
Is Malware Effects Remediation Tool Safe?
Malware Effects Remediation Tool is widely used on Windows operating systems. In terms of safety, it is generally considered to be a safe and reliable software program. However, it’s important to download it from a reputable source, such as the official website or a trusted download site, to ensure that you are getting a genuine version of the software. There have been instances where attackers have used fake or modified versions of software to distribute malware, so it’s essential to be vigilant and cautious when downloading and installing the software. Overall, this software can be considered a safe and useful tool as long as it is used responsibly and obtained from a reputable source.
How to install software from the WinRAR file?
To install an application that is in a WinRAR archive, follow these steps:
- Extract the contents of the WinRAR archive to a folder on your computer. To do this, right-click on the archive and select ”Extract Here” or ”Extract to [folder name]”.”
- Once the contents have been extracted, navigate to the folder where the files were extracted.
- Look for an executable file with a .exeextension. This file is typically the installer for the application.
- Double-click on the executable file to start the installation process. Follow the prompts to complete the installation.
- After the installation is complete, you can launch the application from the Start menu or by double-clicking on the desktop shortcut, if one was created during the installation.
If you encounter any issues during the installation process, such as missing files or compatibility issues, refer to the documentation or support resources for the application for assistance.
Can x86 run on x64?
Yes, x86 programs can run on an x64 system. Most modern x64 systems come with a feature called Windows-on-Windows 64-bit (WoW64), which allows 32-bit (x86) applications to run on 64-bit (x64) versions of Windows.
When you run an x86 program on an x64 system, WoW64 translates the program’s instructions into the appropriate format for the x64 system. This allows the x86 program to run without any issues on the x64 system.
However, it’s important to note that running x86 programs on an x64 system may not be as efficient as running native x64 programs. This is because WoW64 needs to do additional work to translate the program’s instructions, which can result in slower performance. Additionally, some x86 programs may not work properly on an x64 system due to compatibility issues.
What is the verdict?
This app is well-designed and easy to use, with a range of useful features. It performs well and is compatible with most devices. However, may be some room for improvement in terms of security and privacy. Overall, it’s a good choice for those looking for a reliable and functional app.
Download Malware Effects Remediation Tool 4 Latest Version Free
Click on the button given below to download Malware Effects Remediation Tool free setup. It is a complete offline setup for Windows and has excellent compatibility with x86 and x64 architectures.
File Password: 123










